Addressing CMMC Compliance Gaps for Small Businesses
Navigating the complex landscape of CMMC compliance can be a daunting task for small businesses, but with the right strategies, achieving and...
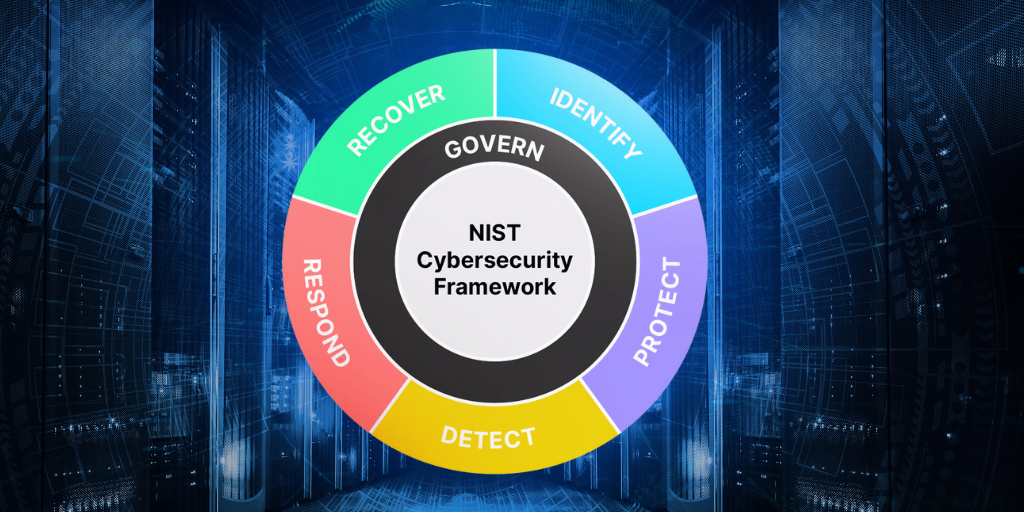
You can explore the latest updates in the NIST CSF 2.0 and understand its security implications and IT teams.
The NIST Cybersecurity Framework (CSF) 2.0 is a set of guidelines and best practices designed to help organizations manage and improve their cybersecurity posture. It provides a common language and framework for organizations to assess and manage cybersecurity risks. The updated version introduces several changes and updates to enhance its effectiveness.
One key aspect of understanding the NIST CSF 2.0 is familiarizing oneself with the core functions. These functions include Identifying, Protecting, Detecting, Responding, and Recovering. Each function represents a specific set of activities that organizations can undertake to strengthen their cybersecurity defenses.
Another vital aspect to understand is the Framework Core. The Framework Core consists of five concurrent and continuous functions necessary for an effective cybersecurity program. These functions are further divided into categories and subcategories that provide more specific guidance on implementing cybersecurity controls.
By understanding the NIST CSF 2.0, organizations can gain insights into their current cybersecurity posture and identify areas for improvement. It is a valuable tool for security and IT teams to align their efforts and prioritize cybersecurity initiatives.
NIST CSF 2.0 introduces critical changes and updates to address the evolving cybersecurity landscape. Some of the notable changes include:
1. Addition of a new category: NIST CSF 2.0 introduces a new category called 'Identity Management and Access Control' to address the growing importance of identity and access management in cybersecurity.
2. Enhanced guidance on supply chain risk management: With the increasing reliance on third-party vendors and suppliers, NIST CSF 2.0 provides expanded guidance on managing supply chain risks.
3. Integration with other cybersecurity frameworks: NIST CSF 2.0 emphasizes the importance of integrating with other cybersecurity frameworks, such as ISO 27001 and CIS Controls, to ensure a comprehensive and holistic approach to cybersecurity.
These changes and updates in NIST CSF 2.0 reflect the evolving threat landscape and aim to provide organizations with more practical guidance for managing cybersecurity risks.
The introduction of NIST CSF 2.0 brings a significant shift in security practices and framework implementation, offering organizations updated guidance and best practices to fortify their cybersecurity stance. Key impacts include:
1. Enhanced risk assessment and management: NIST CSF 2.0 aids organizations in refining their risk assessment and management processes through a structured approach and a common language for discussing cybersecurity risks.
2. Fostering collaboration and information sharing: The framework fosters collaboration and information exchange among security and IT teams, enabling them to collaborate more effectively in combating cybersecurity challenges.
3. Aligning with business objectives: NIST CSF 2.0 assists organizations in aligning their cybersecurity endeavors with overall business objectives, embedding cybersecurity as a crucial element in strategic planning.
4. Simplified compliance endeavors: By embracing NIST CSF 2.0, organizations can simplify their compliance efforts by aligning with recognized industry standards and best practices.
Overall, NIST CSF 2.0's influence on security practices and framework implementation is affirmative, empowering organizations to enhance their cybersecurity capabilities and safeguard their critical assets.
Integrating NIST CSF 2.0 brings challenges and opportunities for IT teams. Embracing the framework demands a deep understanding and adaptation of its guidelines to meet the organization's needs. Adequate resources, encompassing budget, skilled workforce, and technology, are essential for effectively implementing and maintaining the framework. IT teams might need help garnering support and buy-in from senior management and stakeholders, given that implementing NIST CSF 2.0 often necessitates organizational shifts and investments.
Despite these challenges, adopting NIST CSF 2.0 presents numerous opportunities for IT teams to elevate their cybersecurity practices. By adhering to the framework's guidelines, IT teams can proactively enhance the organization's overall cybersecurity posture and fortify defenses against evolving cyber threats. NIST CSF 2.0 is a beacon of standardized cybersecurity practices, empowering IT teams to align their strategies with established best practices and industry standards. Moreover, the framework fosters a culture of collaboration among IT teams and various departments, fostering a more cohesive and efficient response to cybersecurity incidents.
By proactively addressing the challenges and seizing the opportunities presented by adopting NIST CSF 2.0, IT teams can successfully navigate the implementation process and extract maximum value from the framework. Embracing the framework strengthens the organization's cybersecurity resilience and enhances IT team capabilities, positioning them as proactive defenders against cyber threats. IT teams can effectively safeguard critical assets and uphold the organization's cybersecurity integrity through a strategic approach that leverages the framework's guidelines.
When adapting to NIST CSF 2.0, organizations must embark on a meticulous journey of planning and execution. The first step involves conducting a comprehensive gap analysis to pinpoint areas where cybersecurity practices need enhancement and align them with the framework's guidelines. This analysis is a crucial foundation for understanding the organization's security posture and setting the stage for improvement.
Following the gap analysis, the organization should craft a detailed roadmap outlining the steps, timelines, and resources necessary to adopt the NIST CSF 2.0 effectively. This roadmap acts as a guiding light, ensuring the implementation process stays on track and meets the objectives within the defined timeframe.
Engaging stakeholders from various departments, including senior management, IT teams, and business units, is paramount to the success of the implementation process. Securing buy-in and support from these key players ensures alignment across the organization and facilitates a collaborative approach toward enhancing cybersecurity defenses.
Furthermore, it is essential to tailor the framework to suit the organization's unique needs and requirements. This customization involves seamlessly adapting the guidelines and controls to integrate with existing security practices and technologies, maximizing the framework's effectiveness in strengthening the organization's security posture.
Integrating the NIST CSF 2.0 with core organizational processes, such as risk management, incident response, and compliance, is crucial for a smooth and efficient implementation. By embedding the framework into these processes, organizations can ensure a holistic approach to cybersecurity and create a unified front against cyber threats.
Implementing a robust monitoring and review process is critical to sustaining the effectiveness of cybersecurity measures over time. Continuous assessment of these measures allows organizations to stay agile and responsive to evolving threats, making timely adjustments to fortify their defenses and stay ahead of potential security risks.
By adhering to these best practices and embracing the guidance of NIST CSF 2.0, organizations can adapt effectively to the evolving cybersecurity landscape and leverage the framework's benefits to bolster their security defenses and safeguard critical assets.

Navigating the complex landscape of CMMC compliance can be a daunting task for small businesses, but with the right strategies, achieving and...

In an increasingly digital world, non-profits are prime targets for cyber threats. You can just discover how a Virtual CISO can protect your...

Small businesses must prioritize secure messaging to protect sensitive information and maintain customer trust.