2 min read
Executive Cybersecurity Awareness Essentials
Discover why cybersecurity awareness is crucial for executives and how to protect their organizations from cyber threats.
Read More
2 min read
Discover why cybersecurity awareness is crucial for executives and how to protect their organizations from cyber threats.
Read More
4 min read
Discover the key factors and strategies involved in risk assessment within security risk management.

3 min read
You can learn how to protect your valuable data with these essential backup strategies.
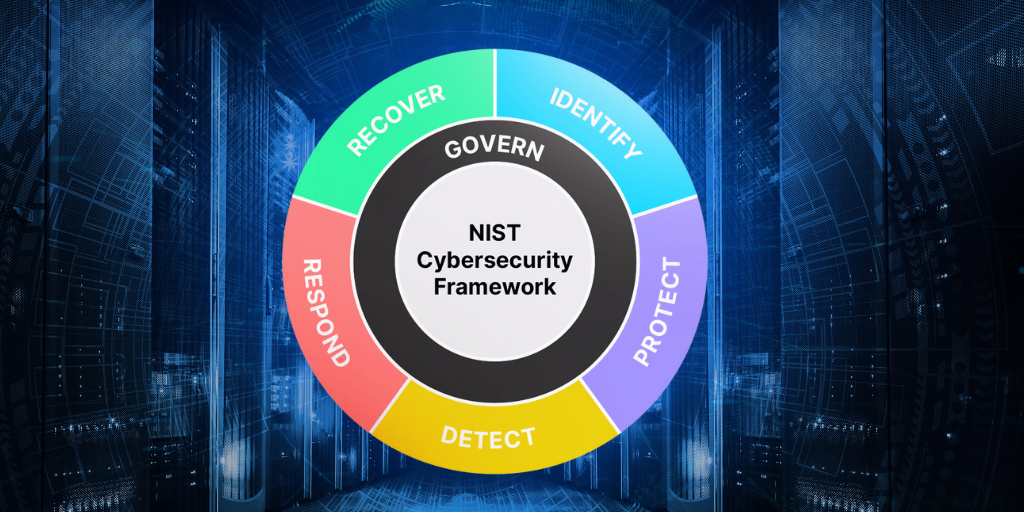
4 min read
You can explore the latest updates in the NIST CSF 2.0 and understand its security implications and IT teams.

2 min read
In today's digital age, the risk of cyber threats looms more significant than ever. Businesses of all sizes, from small startups to large...

1 min read
Businesses nowadays deal with an ever-expanding threat landscape, with cyberattacks posing a persistent concern. As cybercriminals evolve their...

3 min read
In an age where digital threats loom around every virtual corner, cybersecurity is no longer just a concern for tech giants or governmental bodies....

2 min read
The emergence of automated cyberattacks in today's digital environment, driven by what experts call "bad bots", poses a frightening threat to...

2 min read
In the current context of growing cybersecurity concerns, companies are facing an increasing need to obtain SOC 2 accreditation. But what exactly...

1 min read
The electric vehicle (EV) sector is undoubtedly rising, representing a significant shift in the automotive landscape. However, amidst the excitement...