securing the technology
securing the technology
Securing technology within a cybersecurity plan is paramount in safeguarding against evolving digital threats. As technology becomes increasingly integrated into every facet of business operations, it also becomes a prime target for malicious actors. Ensuring the security of technological assets, including networks, systems, and applications, is essential to protect sensitive data, maintain operational integrity, and safeguard against unauthorized access. A robust cybersecurity plan for technology not only mitigates the risk of cyber-attacks but also enhances overall resilience, fostering trust among stakeholders and clients. By prioritizing the security of technology, organizations can navigate the complex landscape of cyber threats with confidence, proactively addressing vulnerabilities and fortifying their digital defenses.

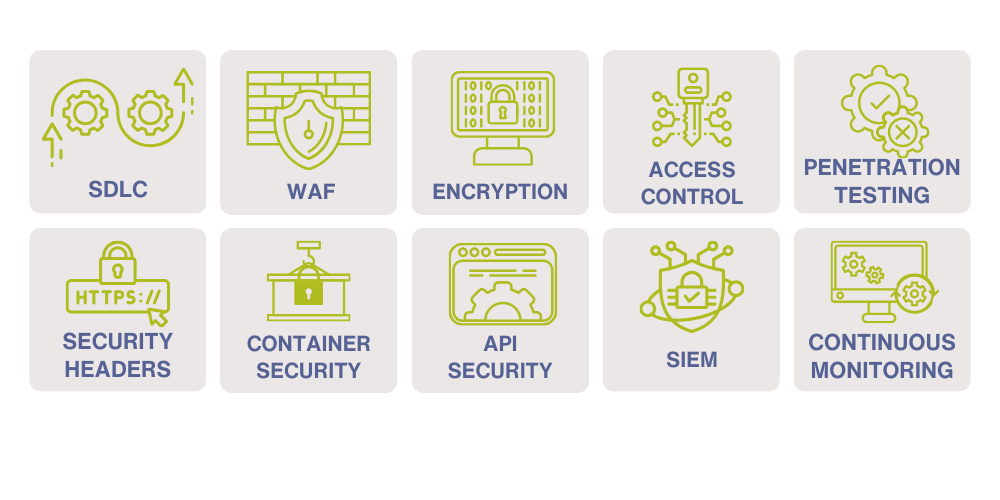
Application Security
Application security refers to the measures taken to secure the applications and software systems that an organization uses. This includes the identification and mitigation of vulnerabilities, such as SQL injection or cross-site scripting, that could be exploited by attackers to gain unauthorized access to sensitive data or systems. Application security is concerned with protecting software applications from unauthorized access, use, disclosure, disruption, modification, or destruction.
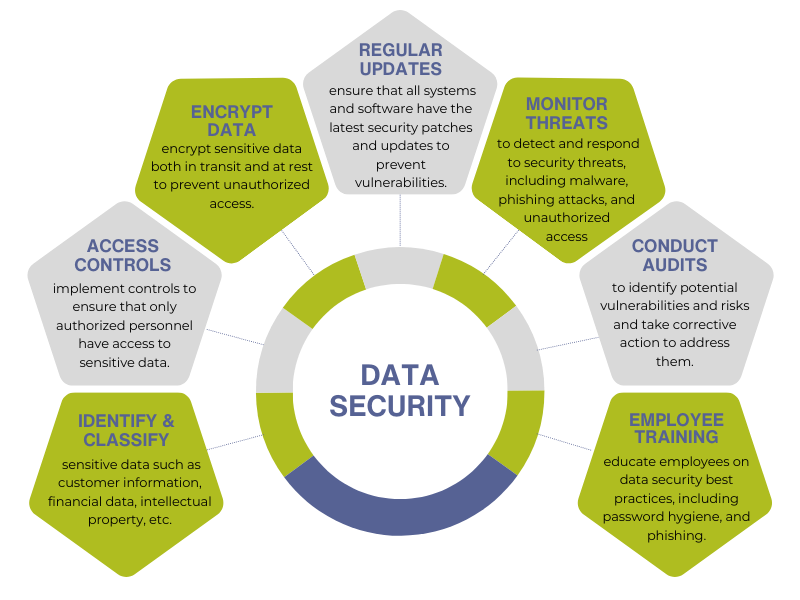
Data Security
Securing data is essential to protect sensitive information from unauthorized access, use, disclosure, or modification.
Here are some key steps to improve data security:
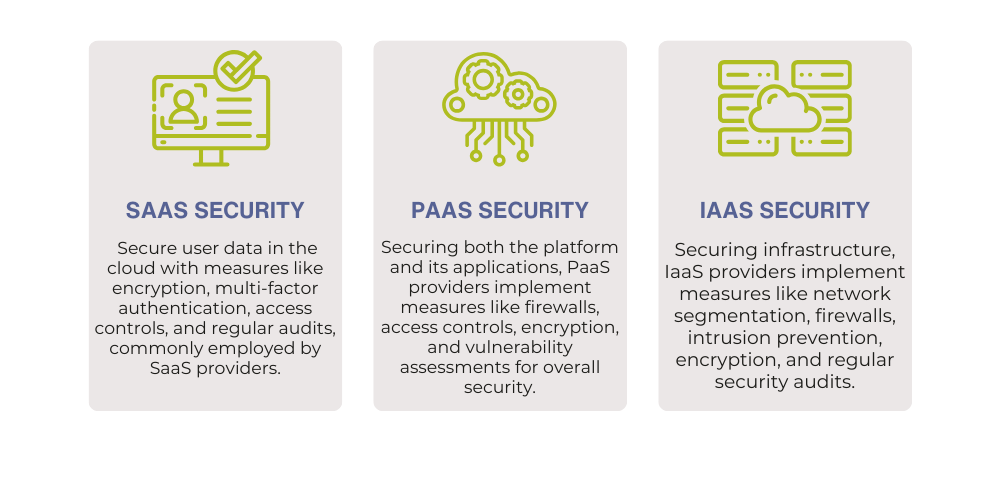
Cloud- Saas/PaaS/ IaaS Security
Cloud computing refers to the delivery of computing services, including servers, storage, databases, networking, software, and analytics, over the Internet. Cloud computing providers offer various types of services, including Software-as-a-Service (SaaS), Platform-as-a-Service (PaaS), and Infrastructure-as-a-Service (IaaS). Security is a crucial aspect of cloud computing, and it is important to understand the security measures in place for SaaS, PaaS, and IaaS.
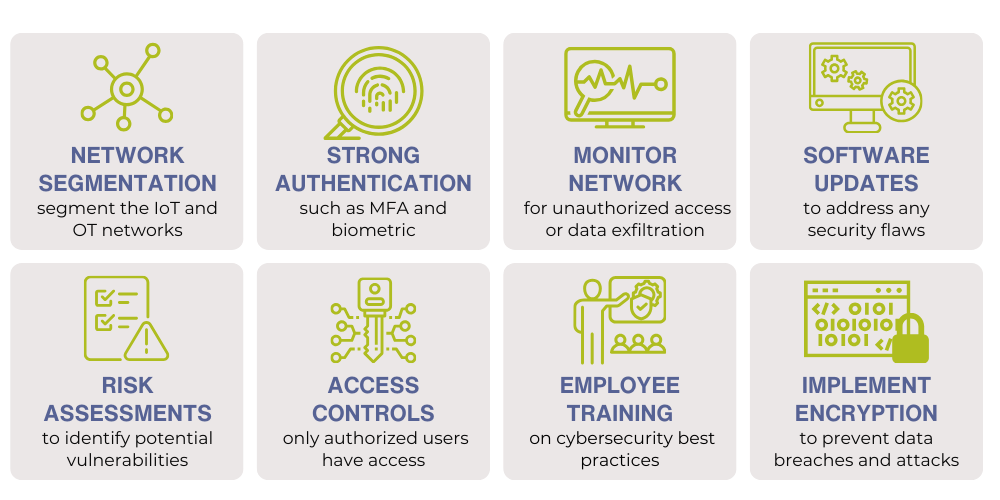
IoT/Operational Technology Security
IoT (Internet of Things) and Operational Technology (OT) security are important topics in today's digital world. IoT refers to the interconnected network of physical devices, vehicles, buildings, and other objects that are embedded with sensors, software, and network connectivity to collect and exchange data. On the other hand, OT refers to the hardware and software that controls the physical devices and processes in industrial control systems (ICS) and critical infrastructure.
The convergence of IT (Information Technology) and OT has increased the risk of cyberattacks on critical infrastructure, such as power grids, transportation systems, and healthcare facilities. Therefore, it is essential to implement robust security measures to protect against these threats.
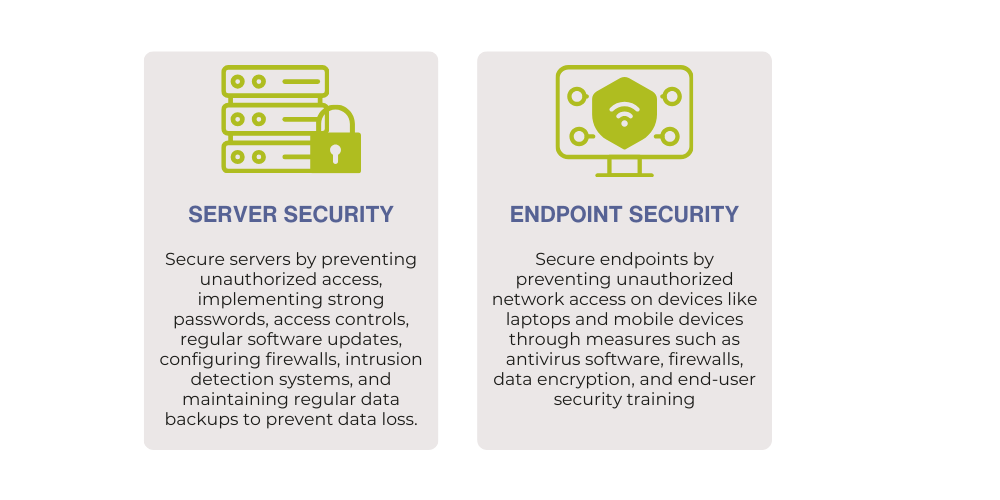
Server & Endpoint Security
Server and endpoint security collaborate to form a robust defense against cyber threats. Servers, acting as organizational pillars, store and manage data, execute applications, and facilitate communication. If a hacker breaches a server, it risks compromising sensitive data, disrupting services, or launching attacks on other systems. Securing servers is crucial to protect business assets. On the other hand, endpoints, including computers and mobile devices, are entry points for cyber threats.
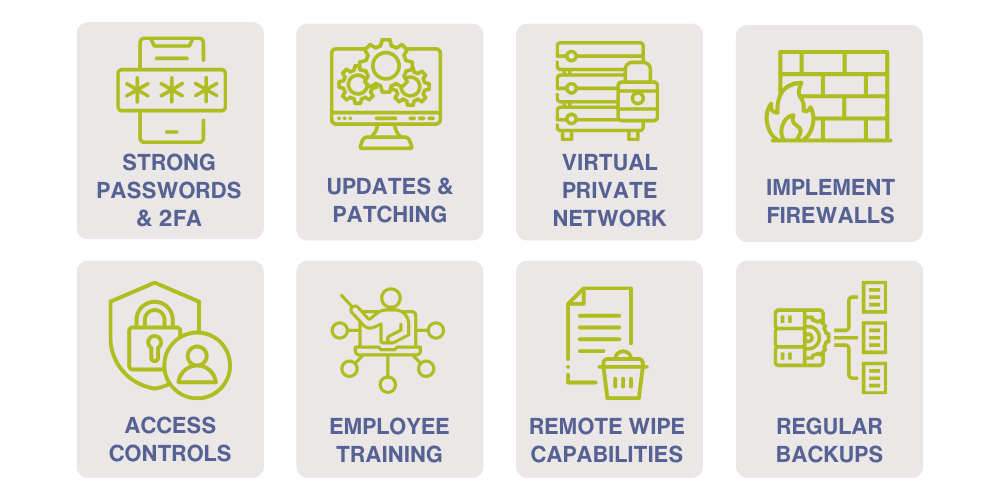
Network & Remote Work Security
Network and remote work security are essential in today's digital landscape. With the increase in remote work and reliance on cloud-based services, it's critical to secure networks and devices to protect sensitive information from cyber threats. Here are some best practices for network and remote work security: